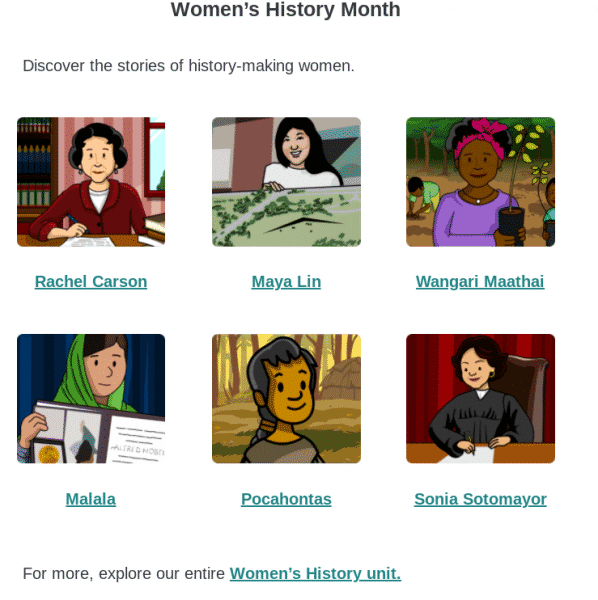
Be on the lookout for scammers trying to impersonate Google. The spammer will take advantage of the option for “Response Receipts.” These emails are sent from the email address “forms-receipts-noreply@google.com.” which is the official, legitimate email.
The spammer pretends the user has filled out something with Google when they have not and requests that the person fill out their email address and click to verify. See an image example below.
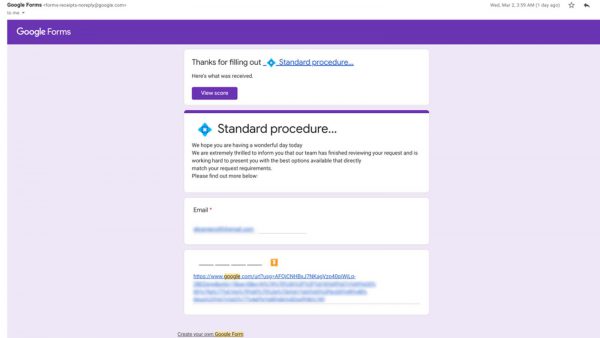
While the email address may be official, those links could lead to anywhere and could ask for more information. Keep in mind, if you are getting a response receipt you likely have already completed what you need and should not need to send any new information.
If you think you have received one of these scam emails, you can click “Report Abuse” at the bottom of the email.
If you would like more details about this scam, please read this post, where we sourced the information for this blog.