As you make plans to close up your classroom for the summer (and enjoy a well deserved break), please note and in some cases, take care of, the following items as the timing dictates:
-
Save, Update, and Share Your Content
- Current Canvas courses will close and get placed in your past enrollments. However, there are considerations to check in the End of Year Canvas Post. Also note Canvas Studio is being Discontinued for 25-26 School Year. If you have videos currently stored in Canvas Studio that you wish to retain, you will need to download them by the end of August (see this blog post for more info).
- If you are leaving the district or hoping to collaborate with colleagues over the summer you might review this post: Sharing Digital Resources with Colleagues – P-CCSK12 Tech
- Clever: Staff and Students will have access to all clever resources throughout the summer. Clever syncing will be on pause starting on Monday June 10, 2025 giving student’s access to their 24-25 teacher’s pages and links until around mid-August when syncing will resume for the 25-26 school year. If you’re interested in learning how to make the most of Clever in your classroom, consider looking at training and ideas here.
- IXL: PCCS’s digital subscription for K-5 elementary students will continue throughout the summer. Students will have access to their NWEA skill plans (which were just updated with any spring scores) all summer. Students will have access to any current teacher starred skills through around mid-August, you might consider un-starring skills for students because they travel with students from year to year. Students in 5th grade currently will lose access around mid-August when syncing begins for the 25-26 school year as they will then be recognized as 6th graders.
- Edpuzzle: AFTER your grades have been transferred to the gradebook, it’s recommended that teachers delete their Edpuzzle classes. Issues can sometimes arise when Canvas courses that were integrated with Edpuzzle are copied from one year to the next. It is recommended that teachers delete their Edpuzzle classes before the new school year starts and new students join your classes. Please follow the directions in Edpuzzle’s Best Practices: Closing Out the School Year.
-
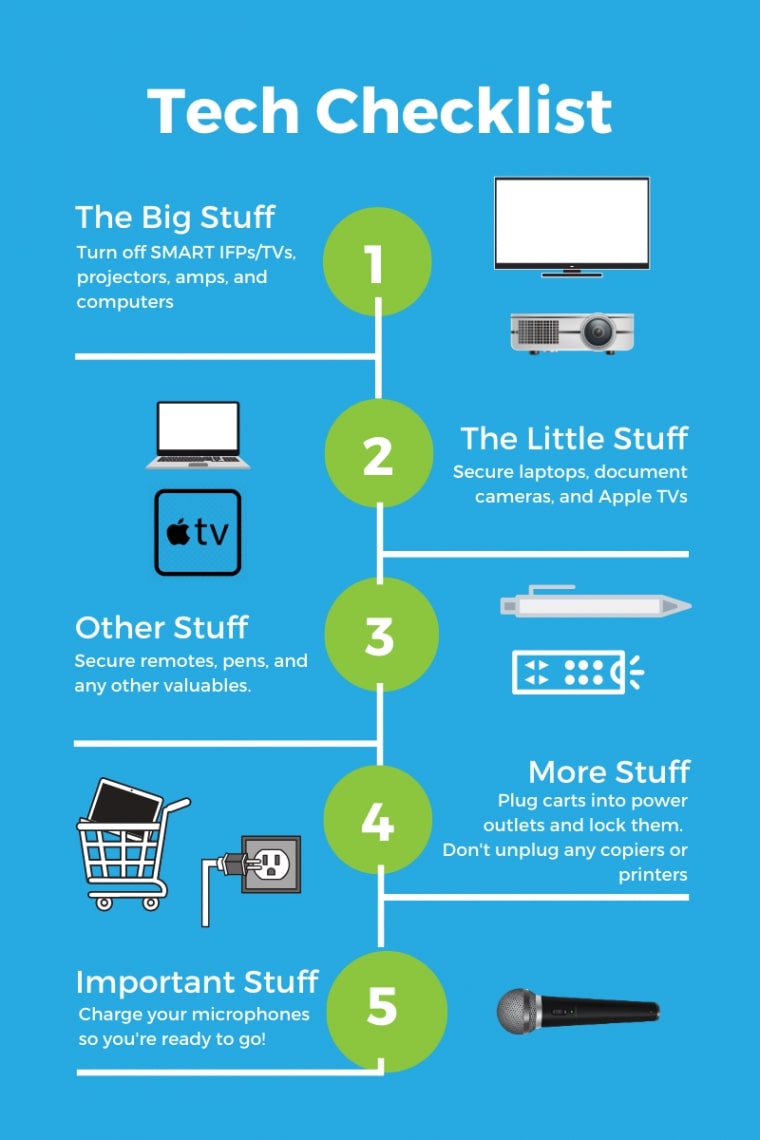
Tech Housekeeping: Secure, Return, and Power Off (typically around the last day of school)
- Please comply with the directions of your principal and main office to turn in or secure all classroom technology equipment such as document cameras, microphones, interactive pens, and remotes.
- Please also secure or take home all District-assigned devices (laptop, Chromebook, iPad, etc.), as well as all personally-owned devices.
- Power off projectors/IFPs, sound amps, and desktop computers.
- You may leave printer and copiers plugged in and powered on
- Follow the care suggestions for classroom audio



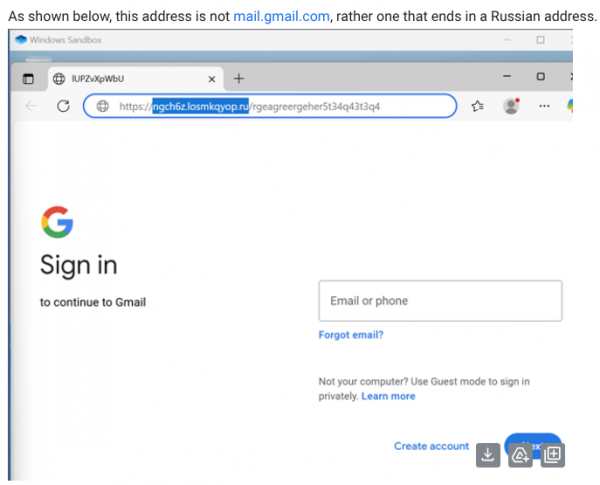

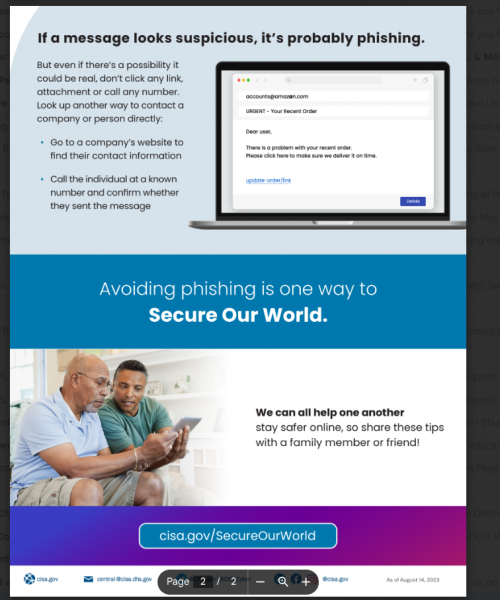

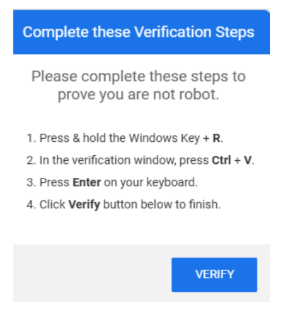
 Phishing is a digital form of social engineering that uses authentic-looking emails to trick users into sharing personal information. It usually includes a link that takes the user to a fake website. If you cannot verify the source, do not open the link. Report suspicious messages to your IT team.
Phishing is a digital form of social engineering that uses authentic-looking emails to trick users into sharing personal information. It usually includes a link that takes the user to a fake website. If you cannot verify the source, do not open the link. Report suspicious messages to your IT team. Social media exploitation is where the attacker uses information found on a user’s social media profiles to create a targeted phishing attack.
Social media exploitation is where the attacker uses information found on a user’s social media profiles to create a targeted phishing attack. Fake IT Support calls are a common form of impersonation where someone pretends to be an authorized user or administrator in an attempt to gain illicit access to protected data systems. The attacker has enough information to sound credible, and they ask the user for some bit of information that will allow the attacker to gain access to the desired system.
Fake IT Support calls are a common form of impersonation where someone pretends to be an authorized user or administrator in an attempt to gain illicit access to protected data systems. The attacker has enough information to sound credible, and they ask the user for some bit of information that will allow the attacker to gain access to the desired system.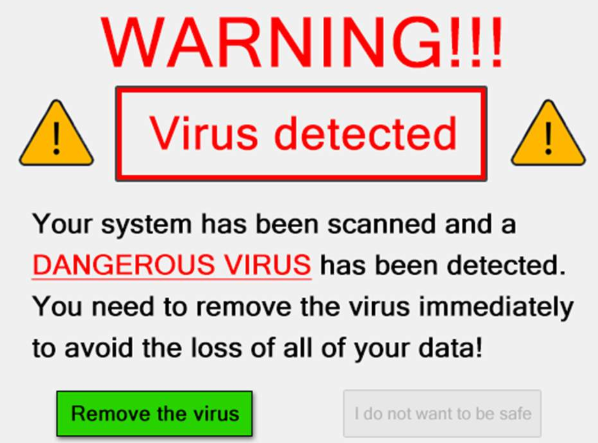 Scareware is a type of baiting where the use of false alarms or fictitious threats lure the user into a trap. One example is the attacker convincing a user that their system is infected with malware and that they should install software granting remote access. Another example is the attacker claiming to have sensitive videos which will be released if the user does not pay.
Scareware is a type of baiting where the use of false alarms or fictitious threats lure the user into a trap. One example is the attacker convincing a user that their system is infected with malware and that they should install software granting remote access. Another example is the attacker claiming to have sensitive videos which will be released if the user does not pay. Tailgating, also known as “piggybacking”, is where an unauthorized person manipulates their way into a restricted area, such as impersonating a well-known role (e.g., delivery driver or custodian worker) or asking a user to “hold the door”.
Tailgating, also known as “piggybacking”, is where an unauthorized person manipulates their way into a restricted area, such as impersonating a well-known role (e.g., delivery driver or custodian worker) or asking a user to “hold the door”. Shoulder surfing is where an unauthorized person stands near a user to get the user’s password or other data from the user’s computer monitor.
Shoulder surfing is where an unauthorized person stands near a user to get the user’s password or other data from the user’s computer monitor.