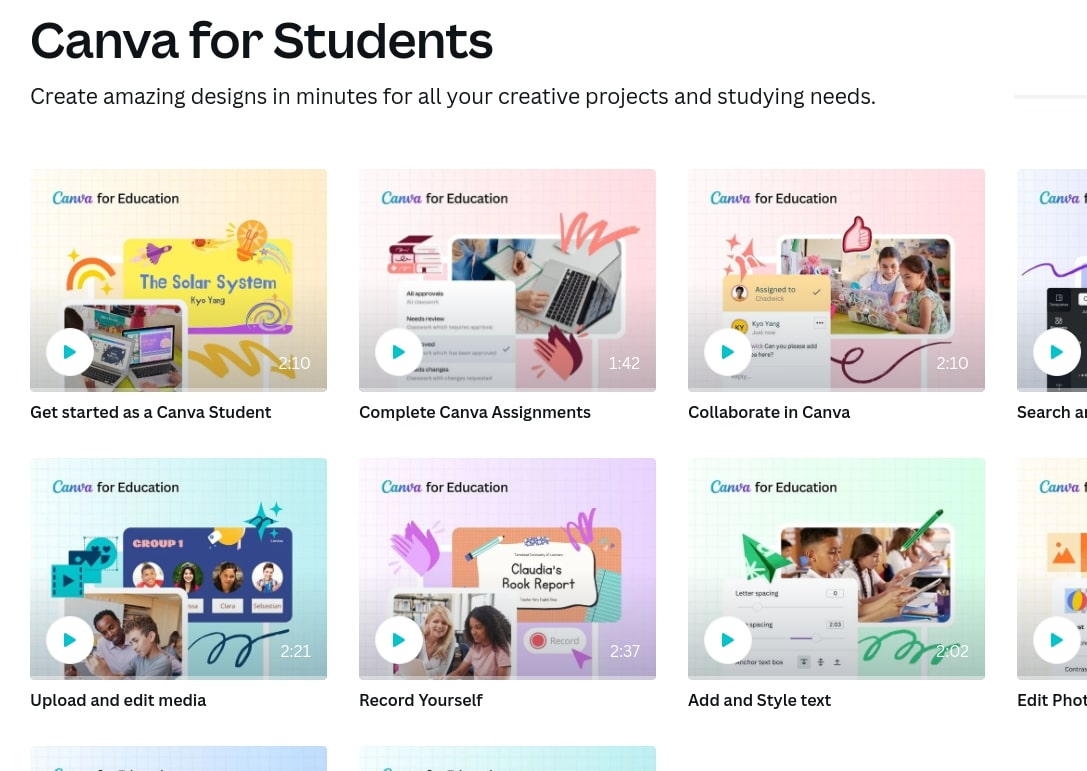
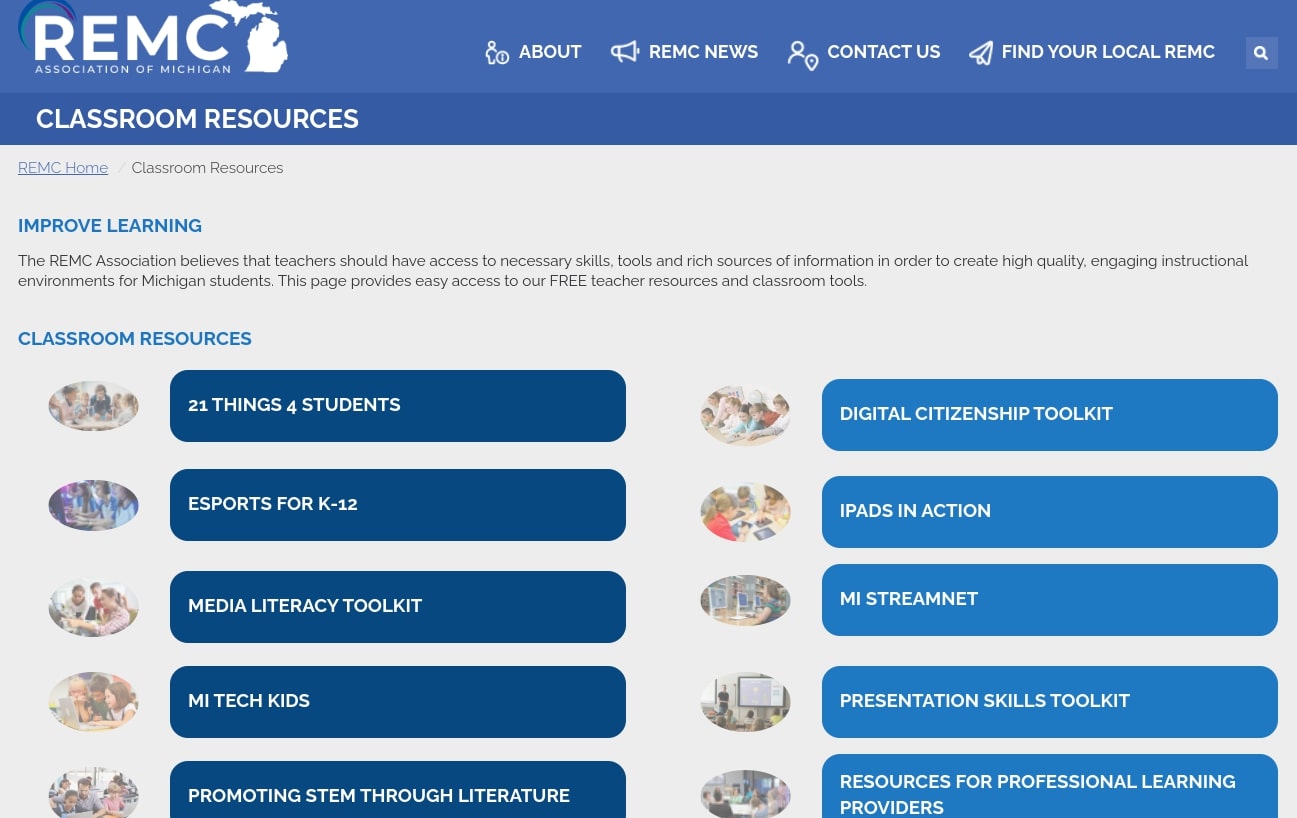
Are you looking for a new classroom tech trick? Need to earn some SCECHs? Look no further than a REMC Course!
Check out May 2022 courses here:
- Formative Assessment Tools that Support Teaching and Learning
- 21Things4Students – Ready, Get Set, Go
- A Practical Guide to Global Success Skills in the Classroom for the 21st Century and Beyond
- Design Thinking Made Practical
- Engaging Students in a Personalized Classroom
- Increasing Efficiency and Productivity
- Multimedia Tools to Engage Students
- PBL for Growing Student Voice
- Preparing Professional Presentations
- Social Media 2: Improve Student Critical Thinking and Collaboration
- Tech Up Your K5 Content with MITECS
Register by Friday, April 29th. You will receive a welcome email with the course login and other information prior to the course starting on May 2nd. If you have questions or need further assistance with your course registration, please contact Erin Rommeck, REMC Event Coordinator.



 You can access your contacts and enter them directly in the correct fields. Then you can draft your email. Because you are in Docs you can share it with your grade-level team or co-teacher for feedback and suggestions.
You can access your contacts and enter them directly in the correct fields. Then you can draft your email. Because you are in Docs you can share it with your grade-level team or co-teacher for feedback and suggestions.