As we continue our efforts to maintain a secure digital environment for our school community, the Technology team would like to provide a timely reminder about phishing awareness and the tools at our disposal.
First, we want to extend our thanks to everyone for your engagement with our KnowBe4 cybersecurity initiatives. Since we began our simulated phishing campaigns, we have seen a positive increase in awareness across our staff. However, the landscape of cyber threats is constantly evolving. Attackers are using more sophisticated and personalized techniques, making it more critical than ever to remain skeptical and vigilant. To put this in perspective, the latest Verizon Data Breach Investigations Report found that 74% of all breaches involved the human element, such as falling for a phishing scam. This highlights that our awareness is truly the first and most effective line of defense.
Our simulated phishing campaigns will continue periodically throughout the school year. Remember, these are not tests designed to catch you out, but rather practical exercises to help us all stay sharp. Think of them as fire drills for our digital safety. The goal remains purely educational: to provide a safe space to practice and hone our skills in identifying and reporting suspicious emails. As before, there will be no disciplinary repercussions for interacting with these simulations. Our focus is on continuous learning and improvement for everyone.
One of the most powerful tools at your disposal is the Phish Alert button. Your active use of this button is essential to our defense strategy. When you report a suspicious email using this feature, you are not just deleting it from your inbox; you are immediately notifying our technology team. This allows us to analyze the threat, block the sender, and remove similar malicious emails from other inboxes across the district, protecting your colleagues before they might even see the threat.
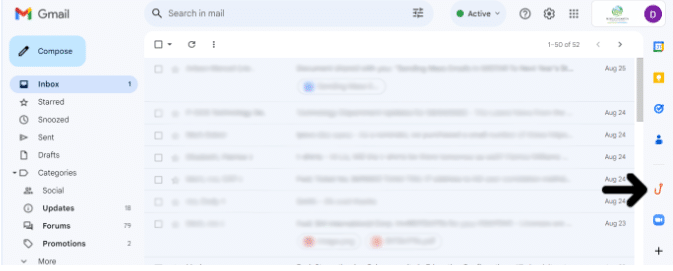
As a quick refresher, the Phish Alert button is located in the Gmail side panel on the right side of your email window, alongside your Calendar and Tasks icons.
We want to address a common question: “What if I’m not sure if an email is a phishing attempt?” The answer is simple: When in doubt, report it! It is always better to be overly cautious. There is no penalty for reporting a legitimate email by mistake. Your vigilance helps create a safer environment for our entire school community, including our students’ data and our shared resources.
Your continued partnership in this effort is crucial. By staying alert and using the tools provided, you are an active participant in safeguarding our institution. Together, we can build a resilient “human firewall” against cyber threats.
Should you have any questions or need a refresher on identifying phishing attempts, please do not hesitate to reach out to our IT department by submitting a service request.
Thank you for your ongoing commitment to keeping our community secure.