As previously shared, the district has a new facilities management system called MasterLibrary Schedules (MLS), which now serves as our replacement for the Virtual Event Management System (EMS).
For those that need to reserve district spaces, please read through this post and familiarize yourself with the basic instructions for logging into, and learning how to use, this new system.
MasterLibrary is currently used within the district for building maintenance and IT requests via ML Workorders. Staff will use their same district Google login credentials when accessing MLS.
MasterLibrary Schedules (MLS) direct link (https://mi50.mlschedules.com)
Once logged in, the facility request procedures are similar to our previous system (EMS). However, to further assist you with navigating the new platform, here are a few resources that you may find helpful:
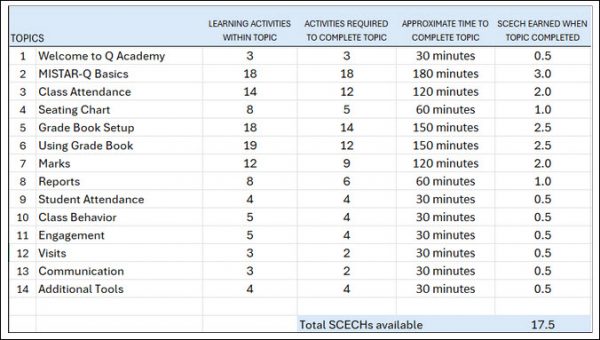
- Basic User Quick Start Guide
- Getting Started Guide – Training Videos, Glossary, FAQ
- Make a Request (Video)
- Using the Calendar
- Additional Reports
To reiterate, effectively immediately, Virtual EMS has been phased out and all staff members must make facility usage requests in MLS by going directly to https://mi50.mlschedules.com (feel free to bookmark), click Log in with Google and sign in with their current district Google account creds. 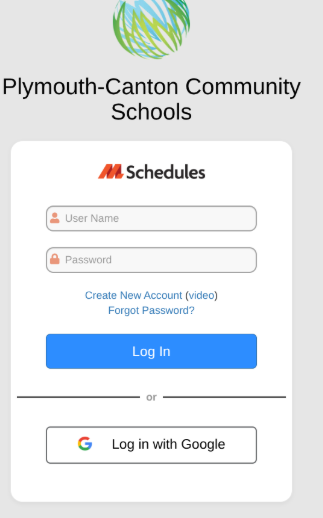
Once your ML Schedules account is created, you can immediately start making facility reservation requests. Booking confirmations or other communications regarding your request(s) will automatically be sent to your district email.
Additional resources:
All requests for building space will need to be made ONLINE directly through MLS and will no longer be processed manually by Facilities.
– For questions or issues relating to booking FACILITIES, please email Marie Rogers.
– For AUDITORIUM / THEATER usage, please email Paul Bird.
– For any technical issues with MLS, please follow the instructions above for reaching out to IT.
Please note, we will be offering several virtual drop-in sessions via Google Meet throughout the month of August for interested staff. Revisit this page as it will be updated with those dates and times.
Thank you in advance for your patience as the district rolls out this new facilities reservation platform. With hundreds of requests coming through on a daily basis, your booking requests and any questions that you may have about MLS will be addressed as quickly as possible.