Effective Monday, March 3, 2025, building assignments for our computer technicians will be adjusted to bring greater efficiency and responsiveness in our work. This change comes as a response to the feedback we have received from staff and analysis of our technology tickets. We expect there may be some challenges as our team transitions to their new building assignments, however, we believe these changes will result in faster response times and resolutions to technology issues.
To assist us with providing you better service, we ask that all technology-related issues be submitted as a Technology Request in ML WorkOrders. We recognize that some staff may prefer to communicate directly with a technology staff member rather than submit a ticket. However, using the ticketing system allows us to effectively manage and respond to everyone’s needs, ensuring no requests are missed or delayed. We are continuously working to improve our technology request system, and we will soon be introducing self-service options that may help you resolve issues even before submitting a ticket.
As a reminder, you can submit a Technology Request ML WorkOrders by going to helpdesk.pccsk12.com or selecting Tech Request Form under the P-CCS Bookmarks folder in Chrome.
We look forward to better serving the needs of the P-CCS community.


 Phishing is a digital form of social engineering that uses authentic-looking emails to trick users into sharing personal information. It usually includes a link that takes the user to a fake website. If you cannot verify the source, do not open the link. Report suspicious messages to your IT team.
Phishing is a digital form of social engineering that uses authentic-looking emails to trick users into sharing personal information. It usually includes a link that takes the user to a fake website. If you cannot verify the source, do not open the link. Report suspicious messages to your IT team. Social media exploitation is where the attacker uses information found on a user’s social media profiles to create a targeted phishing attack.
Social media exploitation is where the attacker uses information found on a user’s social media profiles to create a targeted phishing attack. Fake IT Support calls are a common form of impersonation where someone pretends to be an authorized user or administrator in an attempt to gain illicit access to protected data systems. The attacker has enough information to sound credible, and they ask the user for some bit of information that will allow the attacker to gain access to the desired system.
Fake IT Support calls are a common form of impersonation where someone pretends to be an authorized user or administrator in an attempt to gain illicit access to protected data systems. The attacker has enough information to sound credible, and they ask the user for some bit of information that will allow the attacker to gain access to the desired system.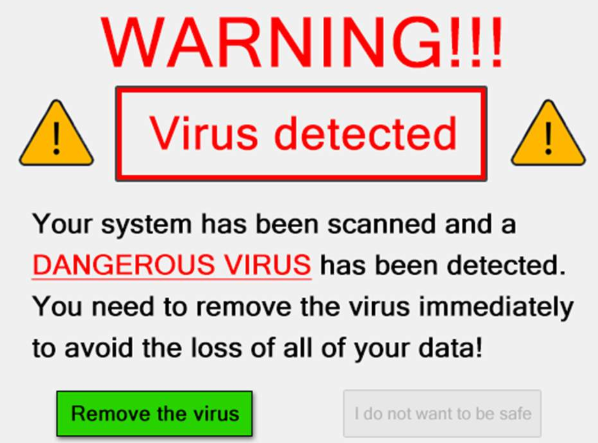 Scareware is a type of baiting where the use of false alarms or fictitious threats lure the user into a trap. One example is the attacker convincing a user that their system is infected with malware and that they should install software granting remote access. Another example is the attacker claiming to have sensitive videos which will be released if the user does not pay.
Scareware is a type of baiting where the use of false alarms or fictitious threats lure the user into a trap. One example is the attacker convincing a user that their system is infected with malware and that they should install software granting remote access. Another example is the attacker claiming to have sensitive videos which will be released if the user does not pay. Tailgating, also known as “piggybacking”, is where an unauthorized person manipulates their way into a restricted area, such as impersonating a well-known role (e.g., delivery driver or custodian worker) or asking a user to “hold the door”.
Tailgating, also known as “piggybacking”, is where an unauthorized person manipulates their way into a restricted area, such as impersonating a well-known role (e.g., delivery driver or custodian worker) or asking a user to “hold the door”. Shoulder surfing is where an unauthorized person stands near a user to get the user’s password or other data from the user’s computer monitor.
Shoulder surfing is where an unauthorized person stands near a user to get the user’s password or other data from the user’s computer monitor.